- news
- ETHICS
AICPA proposes revising independence rules for information system services
Please note: This item is from our archives and was published in 2018. It is provided for historical reference. The content may be out of date and links may no longer function.
Related
AICPA proposes changes to independence guidelines related to private equity
PEEC releases clarifying guidance on independence in SSAE engagements
Navigating outside investors: Safeguarding ethics and independence in evolving practice structures
TOPICS
The AICPA Professional Ethics Executive Committee (PEEC) proposed revisions Thursday to the Code of Professional Conduct (the Code) independence rule that applies to members providing information-systems-related services to attest clients.
These “nonattest” services, which are addressed in today’s Code under Subtopic 1.295, Nonattest Services, raise possible self-review or management participation threats to a member’s independence. The proposed interpretation, “Information System Services,” significantly clarifies and expands upon the current interpretation, “Information Systems Design, Implementation, or Integration” (ET Section 1.295.145).
First, the proposal introduces some new terms, namely:
Financial information system (FIS): An information system that aggregates source data underlying the financial statements or generates information that is significant to the financial statements or financial processes as a whole. To determine significance, members may consider the services’ impact to system controls or outputs subject to attest procedures or a system that:
- Generates data used as inputs to the financial statements;
- Compiles data that help management make decisions that directly impact financial reporting; or
- Is part of the client’s internal controls over financial reporting.
Design of an information system: Determining how a system or transaction will function, process data, and produce results, leading to the development of software code.
Development of an information system: Creating and testing software code.
Commercial off-the-shelf (COTS): A third party’s prepackaged software solution (also referred to as “off the shelf” software) that runs on the client’s computers or in the cloud.
The interpretation addresses systems-related services based on whether they relate to an FIS, hence, the importance of the term financial information system.
Information system is not an FIS
Given the absence of any self-review threat, designing, developing, or implementing a system that is not an FIS does not impair independence if the member satisfies the “General Requirements for Performing Nonattest Services” interpretation (ET Section 1.295.040).
That interpretation requires the member to apply certain safeguards before performing the engagement, to ensure he or she does not assume any of the client’s management responsibilities. Although these requirements apply across the board to all nonattest services a member performs, this proposal emphasizes in several places that compliance with the interpretation hinges on compliance with the general requirements.
Information system is an FIS
The proposal describes the types of activities members may engage in with respect to a client’s FIS, as described in the chart “Design or Develop FIS Software.”
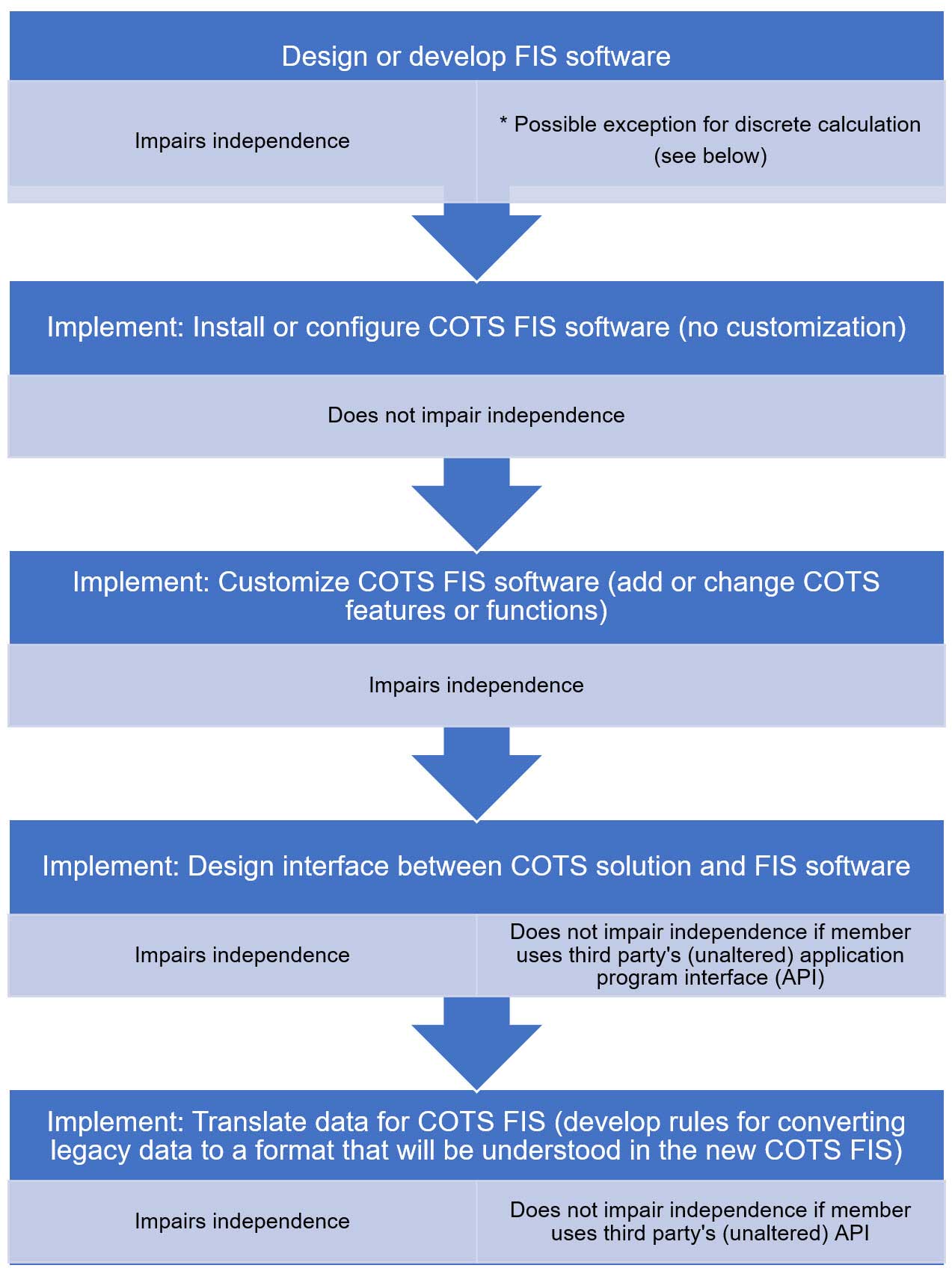
* Per the proposal, a member may design or develop a template that performs a discrete function (e.g., a depreciation calculation) provided the template does not perform an activity that, if performed directly by the member, would impair independence.
System and network maintenance, support, or monitoring
Post-implementation system and network maintenance, support, or monitoring services a member performs on an FIS or other information system may or may not impair independence. If the member takes on a management responsibility for an ongoing function, process, or activity, management participation and self-review threats impair independence. For example, independence is impaired if the member:
- Monitors network performance;
- Manages systems or software applications;
- Manages the client’s information technology (IT) help desk;
- Performs ongoing maintenance (e.g., security, virus protection, or configures user settings); or
- Maintains the security of the attest client’s networks and systems.
However, if the member does not assume management responsibilities and the service is part of a discrete, nonrecurring activity, independence would not be impaired. For example, independence would not be impaired if the member:
- Analyzes the network and provides advice and recommendations;
- Applies virus solutions, system updates, or patches (member did not design or develop the solution);
- Trains client personnel on a new software application;
- Evaluates the design or operating effectiveness of IT security controls; or
- Evaluates IT security policies and practices.
Though the revised rules mainly clarify and explain the existing rules, two substantive changes from the current interpretation are reflected in the proposal:
- Applying the definition of an FIS (i.e., considering whether the results of the services will have a significant impact on the financial statements or processes) could result in a less restrictive interpretation than the current standard, which is silent on what constitutes an FIS, and therefore bans all design or development services for an FIS regardless of magnitude.
- Greater clarity on the types of network maintenance activities members may perform, with a focus on performing one-off services versus continuing maintenance, will likely lead to more activities impairing independence than the existing standard.
Comments on the proposed interpretation are due June 15 and can be emailed to Ethics-ExposureDraft@aicpa-cima.com. If adopted, the final interpretation would become effective one year after the interpretation is published in the JofA.
— Catherine R. Allen (callen@auditconduct.com) specializes in ethics and independence through her consulting firm at Audit Conduct LLC in Rocky Point, N.Y. To comment on this article or to suggest an idea for another article, contact Ken Tysiac, a JofA editorial director, at Kenneth.Tysiac@aicpa-cima.com or 919-402-2112.Integration)


















