- column
- TECHNOLOGY Q&A
Take refuge in a password manager
Related
AI early adopters pull ahead but face rising risk, global report finds
COSO creates audit-ready guidance for governing generative AI
AI loses ground to pros as taxpayers rethink who should do their taxes
Q. I have been using my internet browser’s built-in password manager. I see products that are dedicated for saving passwords. Why should I use one of those applications instead of the browser, and what features should I be looking for in such an application?
A. Internet browsers’ ability to save passwords is an easy and convenient tool, but saving passwords is different from managing passwords. First, browsers will encrypt the password that is being used, but the key to that encryption is stored on the computer. This is the digital equivalent of putting a sticky note on a monitor that has a computer password. Next, there is less cross-platform support; the same browser would need to be used across all devices. Lastly, password managers have additional features a browser lacks that can make your life easier, such as a customized password generator and built-in authenticator for six-digit codes. There are a number of password managers, but I use Bitwarden.
Before I get into features to look for in a password manager, I want to summarize the recent breach of LastPass, why it is concerning, and some best practices in implementing a password manager. Password managers store passwords for a user in a data vault, and in 2022 hackers stole the vaults for 30 million LastPass users. This data included encrypted usernames, encrypted passwords, URLs of websites for those credentials, and metadata such as when a set of credentials was used. With URLs and metadata being unencrypted, the hackers know what websites a user was accessing, such as a bank name, and how recently the bank was accessed, which is very worrisome.
Since we are allowing these applications to manage the keys to all our lives, it is important to understand the encryption process.
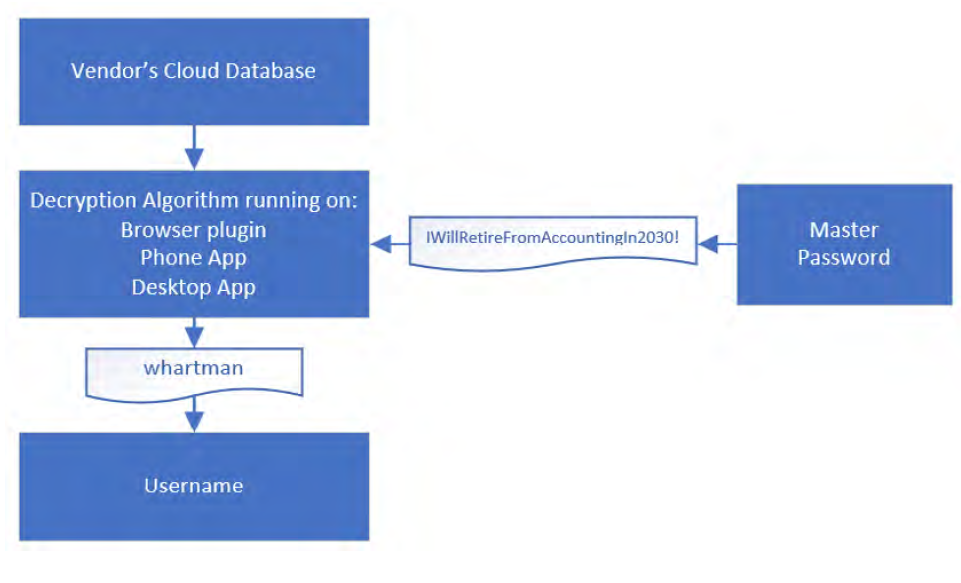
The process of encryption is based on taking data such as a username and feeding the data along with the master password into an encryption algorithm. The algorithm scrambles the data with the master password into what looks like random text, but it is encrypted data. Password managers store this encrypted data. The encryption is only as strong as the master password, and a weak master password results in weak encryption. A long, complex master password gives the computer algorithm more to scramble with, resulting in stronger encryption. Below is a diagram that illustrates the process.

To decrypt, the process is reversed with the encrypted data and the master password being fed back into the algorithm to show the username. The diagram below shows this process.
When selecting and using a password manager, here are some best security practices:
- The password manager should encrypt everything, not just usernames and passwords.
- The password manager should have a zero-knowledge model with end-to-end encryption. Zero knowledge is when all data the manager stores is encrypted. End-to-end encryption means that the encryption happens on the device and only the scrambled data is sent to the password manager. Decryption also happens on the device.
- Use a passphrase because it will be easy to remember but hard to crack for a hacker. “IWillRetireFromAccountingIn2030!” is 32 characters, is easy to remember because it is a goal, and includes uppercase letters, lowercase letters, numbers, and symbols.
- Don’t use any personal information in your master password. Social media has made personal information easily accessible.
- Don’t use the master password anywhere else. If you use the master password on other websites and they get compromised, then the master password is now compromised also.
- Let the password manager create passwords. The manager will create a strong password and allow the manager to create different passwords for every website. If I need to access the site, but don’t have access to the vault, I will use the Forgot Password link that the website has.
- Only unlock the vault using the master password or, in the case of a phone, biometrics. There are cases of social engineering in which a bad actor will watch a person unlock their phone using a PIN and then steal the phone. This could enable the thief to access information and apps on the phone that aren’t protected by biometrics.
All password managers will start with a plug-in installed on your internet browser. This plug-in will populate your passwords into the websites you visit.
The first feature I would like to look at is the password generator. I like Bitwarden’s generator because I can set options based on a website’s password requirement (see the screenshot below).
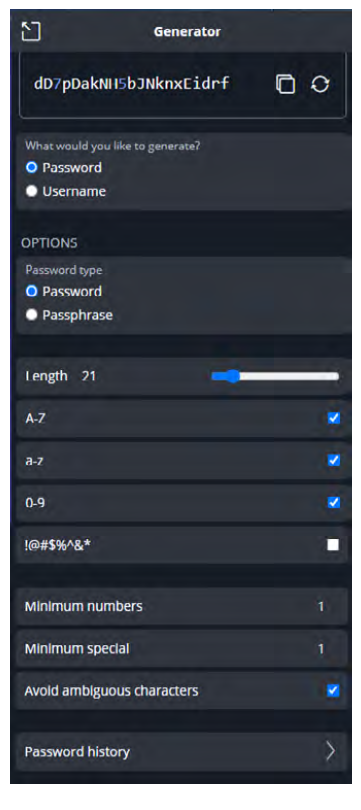
Each website may have different requirements. Certain special characters may not be allowed in a password. With the different options, I can generate a password that conforms to the requirements but is still secure. Additionally, I don’t have to think of a random password, so that’s one less decision I need to make in a day.
The next feature I’ll explore is using Bitwarden to manage my authenticator codes. When I set up multifactor authentication using a QR code, I log the text code into Bitwarden. Below those QR codes will be an option to use a text code (see the screenshot below).

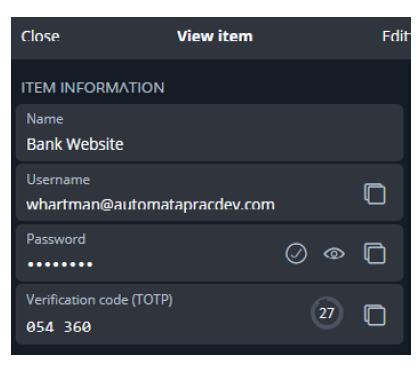
When I click on the link, I will be given a string of text that looks something like this: amsz kymy 2w3h x6l2 fcs7 oao6 qtyr auy2. I will enter that text code into the authenticator key (TOTP) field of Bitwarden (see the screenshot below). With that, I can generate the six-digit number when logging in to a website.
Now that I have populated my vault with some information, I can download the Bitwarden app to my mobile device and log in with my master password. This cross-platform functionality gives the phone’s internet browser access to the vault, regardless of my using Microsoft Edge on my computer or Google Chrome on my phone. Before doing anything else, I go into the app’s settings, and I turn on biometrics so my phone can use a fingerprint to unlock the vault.
The final feature I like is Bitwarden’s ability to store what it calls “identities” — personal information that Bitwarden can fill in on online forms — and the ability to attach files such as scans of a passport or driver’s license. This is a paid feature for most vendors.
About the author
Wesley Hartman is founder at Automata Practice Development and director of technology at Kirsch Kohn & Bridge LLP.
Submit a question
Do you have technology questions for this column? Or, after reading an answer, do you have a better solution? Send them to jofatech@aicpa.org. We regret being unable to individually answer all submitted questions.


















