- feature
- PRACTICE MANAGEMENT
Accounting firm data breaches: One state’s records
Find out the most common types of breaches and how to guard against them all.
Please note: This item is from our archives and was published in 2019. It is provided for historical reference. The content may be out of date and links may no longer function.

Related
IRS should open Trump accounts for eligible children automatically, AICPA says
AI early adopters pull ahead but face rising risk, global report finds
COSO creates audit-ready guidance for governing generative AI
Because accounting firms provide tax compliance and advisory services, they must retain their clients’ Social Security numbers (SSNs). That information is valuable to external hackers, who can sell it on the black market to criminals intent on committing tax refund fraud or other fraud.
The IRS has warned firms of the security risks of having such valuable information (see FS-2017-04, available at irs.gov). But how many accounting firms have truly experienced a data breach? Is your firm a target? And what can your firm do to prepare for and to recover from a data breach or other cyber event?
DATA BREACH REPORTING
All states have laws requiring firms to report information concerning data breaches. In most cases, businesses must report breaches to the state attorney general’s office. Several of these states publish information online about the breaches in order to be transparent to the public. For 11 states, information about individual data breaches is posted on a state-maintained website. Media reports and government data are combined on private websites, such as privacyrights.org, to present a more comprehensive national picture of data breach activity.
Since data breach reporting laws vary by state, it is difficult to see the whole picture across the country. The data collected by each state vary in the number of residents affected, the type of information compromised, and the timing of the report. This article focuses on one state, Maryland, which discloses breach information on its public website, to examine the reported breach activity for accounting firms.
Maryland is unique because in addition to the date of the breach, it reports the type of breach and identifies the specific data elements compromised. It also links to documents the reporting entity submitted to the state, which allows the public to learn nuances about the breaches that are not immediately evident from the classification. Most importantly, entities report a breach even if only one Maryland resident is affected.
Our examination of Maryland data from January 2014 to February 2018 reveals much about public accounting firm data breaches. During this period, we identified 132 accounting firm breaches in which approximately 90% of the firms involved are smaller than the largest 300 accounting firms by revenue.
As seen in the table “Number of Accounting Firm Incidents, by Type,” the top three categories for type of breach are unauthorized access (someone either internal or external to the organization somehow viewed information inappropriately), hacking (an outsider to the organization accessed the data without permission), and unknown (or blank — meaning not disclosed).
Number of accounting firm incidents, by type
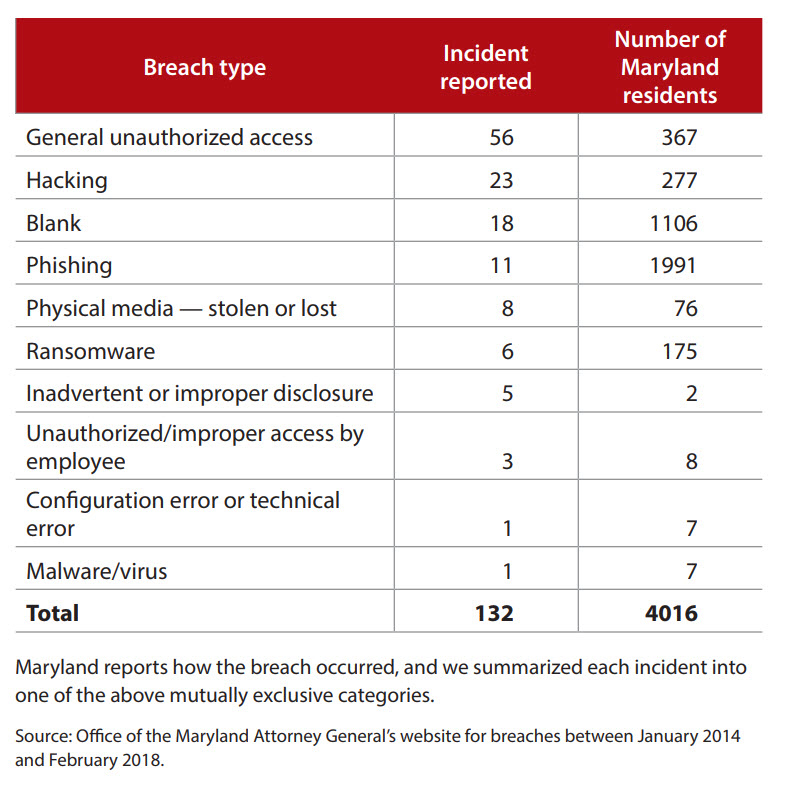
It is disconcerting that the third most frequent categorization based on the number of incidents reported is essentially unknown. Moreover, the number of Maryland residents affected is reported to have been over 1,100, which is nearly double the number of Maryland residents affected by the first two categories combined. Since targets of 14% of data breaches do not provide information on the number of Maryland residents affected, and Maryland only requires firms to report the number of Maryland residents affected, these numbers understate the impact of these data breaches, both in Maryland and across the country. The inability to provide a categorization suggests the existence of a data compromise but an inability to know the details behind the breach by the time it is reported. The large number of incidents in the unknown category highlights that forensic IT specialists often need to be called in to autopsy the incident to help firms better understand their current and future risks.
Since some categories of breach specifically involve employee actions (i.e., inadvertent disclosure, unauthorized access by an employee or a former employee, etc.), the blank or unknown classification makes it difficult to determine if the breach originates from an internal or external source. Thus, without knowing the source of the breach, it is difficult to ensure that correct controls are implemented to reduce the future risk of a breach. In contrast, the data reveal that phishing attacks appear to affect the most Maryland residents.
TREND OF DATA BREACHED
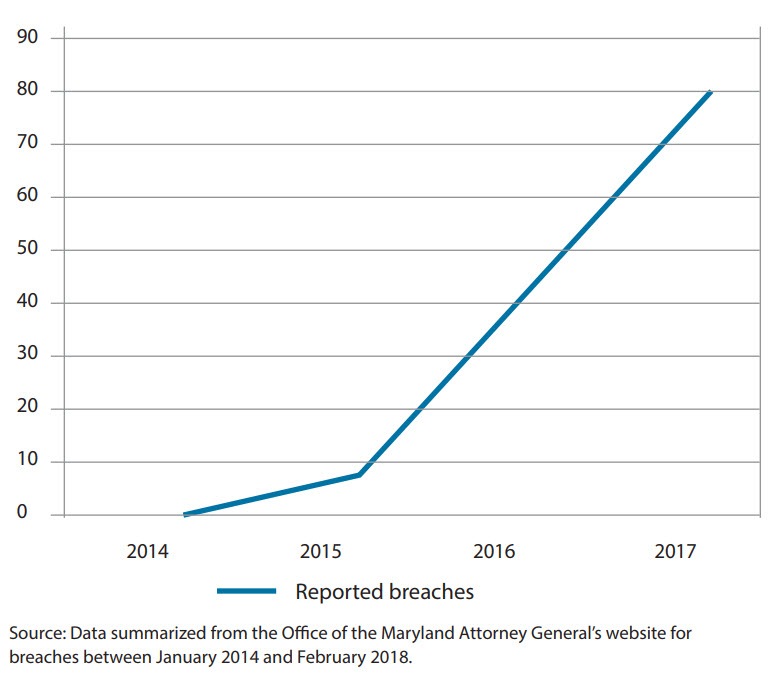
In addition to examining the types of breaches, we also examined a time trend of data breach activities among accounting firms (see the chart “Trend of Reported Breaches for Accounting Firms”). The number of reported breaches increased from zero in 2014 to seven in 2015, 41 in 2016, and 79 in 2017. Unfortunately, this time trend reflects a troubling, increasing trajectory for accounting firm information breaches. While not all of these breaches involved malicious attempts to obtain information — some were inadvertent — the upward trend suggests an increased threat to the information gathered and maintained by accounting firms. There can be a significant delay from when the firm notifies the state until the public disclosure of a breach on the state’s website. Thus, the threat may be more pronounced than these historical data reveal.
Trend of reported breaches for accounting firms
MANY STATES ARE EXPERIENCING DATA BREACHES
Because even small accounting firms may have clients with filing requirements in many states, they often are providing services to a large region and may even be providing services nationally. Therefore, it is not surprising that, despite examining only Maryland’s database, we identified accounting firms based in about two dozen states in the sample.
Because each state has different requirements on what, when, and how data breaches are reported, and because each investigation follows its own path, it can be difficult to consistently identify unique breaches across various government websites. For example, if a firm first determines that it triggers Maryland reporting requirements and then the investigation reveals required reporting for California, the actual data reported to each state may not be identical, even if the information all comes from a single breach.
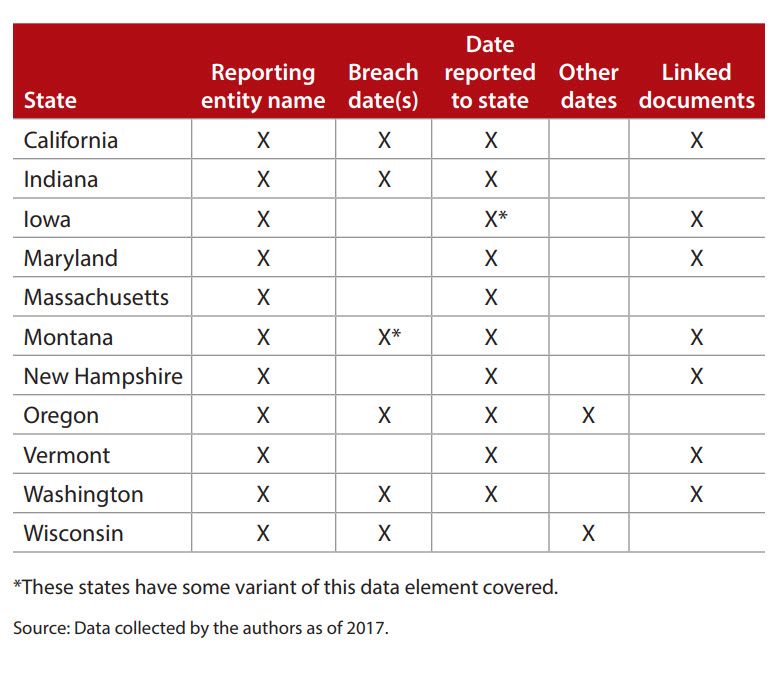
For an accounting firm, an analysis of client addresses before any breach event may reveal the breadth of required reporting if a breach were to occur, enabling timely reporting to each state that a firm is required to report to. The table “Data Required to Be Disclosed, by State” summarizes those states with public transparency of data breaches and the respective data elements.
Data required to be disclosed, by state
TYPES OF DATA ACCESSED DURING A BREACH
Data accessed appear to be connected either to the business side (e.g., credit card payments from customers) or activities of an accounting firm — mostly tax with one specifically audit-related breach identified (Office of the Maryland Attorney General, available at marylandattorneygeneral.gov. The majority of accounting firm breaches compromised SSNs, with half of these including other tax information.
Only seven of the 132 accounting firm breaches, approximately 5%, appeared to compromise credit card or password information. In contrast, of all nonaccounting firm data breaches reported in Maryland, almost 34% related to credit card, health care, or password information, or were missing the data elements breached (781 breaches). Also, these other entities had breaches approximating a 40/60 split between tax information and Social Security breaches from a total of 1,423 breaches. Based on the data from Maryland, while accounting firm breaches appear to involve tax information more often, corporations, not-for-profits, and government entities also have challenges in protecting tax-related data, mostly related to employees.
It is important to note that many firms report breaches out of an abundance of caution even though they have no evidence that any harm was done. This reflects the reality that it is difficult to follow data usage once the information leaves the firm. Nonetheless, the harsh reality of the frequent occurrences of data breaches is that the question is when a firm will be subject to a data breach, not if a firm will be subject to one.
IMPORTANCE OF CONTROLS
In an era of breach fatigue, when people fail to change their post-breach behavior due to the numbing effect of so many breaches, it is important for accounting firms to realize the risks they face and take preventive actions to limit exposure to data breaches. IRS Publication 4557, Safeguarding Taxpayer Data, has helpful suggestions for actions taxpayers and tax preparers should take to secure taxpayer data. These key actions begin with maintaining your systems (i.e., keeping them current with patch management) and solid IT controls (i.e., firewalls, encrypting all data, network monitoring, backup and recovery plans, and air gap backups where the backup is not accessible remotely or connected to the internet). It also requires support from the top management of the company — a prioritization of information security throughout the organization.
Firms can use technology such as encryption to reduce the value of data if they are breached, as criminals have to decrypt the data for them to be useful. Encryption can also be one reason that a firm may not have to report a data breach to the authorities, as it can be a stated exception (see “State Data Security Breach Notification Laws,” available at mintz.com). Thus, security decisions may have broader repercussions than solely protecting the firm’s data.
Accounting firms can take a variety of preventive actions, including ensuring employees are aware of their role in information security for physical devices or property (i.e., laptops, flash drives, paper, etc.), monitoring compliance with company policies on data retention and storage, and educating employees on how to protect against phishing or other information disclosure attempts. These people-focused actions assist in managing the “people” risk that underlies many inadvertent or employee error breaches along with some malware or virus incidents.
As the data reveal, it is not always easy to determine when and how your system is affected, especially to the data element level. Partners can consider internal monitoring tools and even monitoring third-party sites to uncover discussions about their firm’s data. Additionally, a growing area of concern is the tendency for employees to create shadow IT systems, where they own the hardware and can access the firm’s systems using their personal devices (see “The Impact of Shadow IT Systems on Perceived Information Credibility and Managerial Decision Making,” by Noah Myers, Matthew W. Starliper, Scott L. Summers, and David A. Wood, Accounting Horizons, Volume 31, Issue 3 (September 2017), available at aaapubs.org).
Challenges can arise from these shadow IT systems, as employees are able to access information stored on the cloud from anywhere on any device, provided they have the access codes. Accounting firms may need to implement policies that require employees to use only firm-provided and firm-approved devices, including cloud devices where available, since firms have less control over security updates on these shadow IT systems than on firm-approved devices.
Accounting firms also need to realize the importance of having a corrective plan in place, which often requires a firm to do tabletop exercises and drill employees on how to react to a breach. For example, what actions are necessary if a virus infects the system, executing a ransomware attack? Client service personnel need to know what actions to take and how to work without the system while backups are restored and forensic specialists are contacted. The forensic specialists that will be contacted should be determined before a breach occurs, not after, as any delay in correcting the data breach can be extremely costly given the information’s sensitive nature. The firm can react more effectively to a data breach by practicing the response plan.
Beyond testing the incident response plan, best practices promote cyber wargaming, which involves a simulated incident to which firm personnel must respond. This type of activity raises employee awareness of the latest type of attacks and threats and requires them to react appropriately to an event.
Debriefs after the cyber wargame can identify weaknesses in implementing the response plan. This type of activity takes more time to plan and execute than tabletop exercises but may yield significant benefits if additional weaknesses can be identified and remediated before a data breach occurs (e.g., see “Prepare for the Unexpected,” Deloitte, available at www2.deloitte.com).
Accounting firms can also consider other corrective measures, such as breach insurance or specific insurance riders for cybersecurity incidents, if warranted (see “Professional Liability Spotlight: Cyber Liability: Managing Evolving Exposures,” JofA, Jan. 2019). Firm personnel can spend significant time after a breach recovering and re-creating work, along with managing client relationships — time that cannot be billed. In total, a breach’s direct and indirect costs can add up to significant dollars.
For example, customers may sue the firm for failing to keep the information safe (see “User Compensation as a Data Breach Recovery Action,” MIS Quarterly, available at vvenkatesh.com). Also, since breach insurance requires the firm to take specific actions to comply with the insurance policy, small accounting firms may find breach insurance particularly valuable in identifying efficient ways to invest in their information security.
Finally, detective controls need to be put in place to ensure that breaches are identified quickly. These controls include monitoring data files for unusual activity patterns, configuring alerts for unusual network and data traffic patterns, or examining external traffic for unusual email addresses or activity. However, since hackers are continually developing new scam techniques, even the best detective controls may not promptly catch all breach attempts.
REPUTATIONAL RISKS
While the IRS reports a downward trend in tax fraud identity theft cases (see “Tax Practice Corner: The War on Tax ID Theft Continues: CPAs’ Role,” JofA, Aug. 2017), the reputational threat to an accounting firm of identity theft arguably continues to increase, and the baseline for meeting professional standards continues to rise. Accounting firms not only have to consider the negative effects that a data breach could have on their reputation, but also the possibility that they will be found to have violated their professional responsibility to not disclose confidential client information under the AICPA Code of Professional Conduct.
LOOKING AHEAD
While these discussions represent the current technological environment’s potential to affect accounting firms’ data security measures, the certainty remains that technology will continue to advance, and accounting firms must continue to invest in data security measures, in both technology and personnel, to protect against a variety of attacks. Unfortunately, no single magic bullet exists to keep client records safe. We suggested earlier several best practices that companies should employ, including ensuring solid IT controls, encryption technology, employee education, and cyber wargaming. A multipronged approach using these best practices along with continually educating employees about their role in securing information will convey an appropriate tone from the top to permeate the organization. If the money and time are not invested in information security, the firm’s reputation will be affected when clients need to spend their time and money in remediation after their identity has been compromised — with or without a fraudulent tax return filed.
About the authors
Christine Cheng, Ph.D., is an assistant professor of accounting at the University of Mississippi in Oxford, Miss. Renee Flasher, CPA, Ph.D., is an assistant professor of accounting at Penn State Harrisburg in Middletown, Pa. James P. Higgins, CPA, CGMA, is a partner with LWG CPAs & Advisors in Indianapolis.
To comment on this article or to suggest an idea for another article, contact Sally P. Schreiber, a JofA senior editor, at Sally.Schreiber@aicpa-cima.com or 919-402-4828.
AICPA resources
Articles
- “Professional Liability Spotlight: Cyber Liability: Managing Evolving Exposures,” JofA, Jan. 2019
- “Professional Liability Spotlight: Shore Up Your Data Breach Detection Skills,” JofA, Oct. 2018
- “Tax Practice Corner: The War on Tax ID Theft Continues: CPAs’ Role,” JofA, Aug. 2017
- “Tax Practice Responsibilities: Safeguarding Confidential Client Information: AICPA and IRS guidance,” The Tax Adviser, May 2017
- “Tax Practice Corner: Keeping Clients’ Tax Data Secure,” JofA, Oct. 2016
Publication
- Protecting Yourself From Tax ID Theft (brochure), aicpa.org (AICPA member login required)
CPE self-study
- Protecting Your Client and Your Firm From Tax Return Identity Theft (#166091, online access)
For more information or to make a purchase, go to aicpastore.com or call the Institute at 888-777-7077.
Web resources
- AICPA Cybersecurity Resource Center, aicpa.org
- AICPA ID Theft Checklist for Clients: Action Steps for Recovery, available at aicpa.org (AICPA member login required)
The Tax Adviser and Tax Section
Subscribe to the award-winning magazine The Tax Adviser. AICPA Tax Section members receive a subscription in addition to access to a tax resource library, member-only newsletter, and four free webcasts. The Tax Section is leading tax forward with the latest news, tools, webcasts, client support, and more. Learn more at AICPAStore.com/taxsection. The current issue of The Tax Adviser and many other resources are available at thetaxadviser.com.
OTHER RESOURCES
Website
Identity Theft Information for Tax Professionals, IRS web resource


















