- feature
- FRAUD
Round numbers: A fingerprint of fraud
Auditors and forensic accountants are among the CPAs who can benefit from an understanding of when the overuse of certain numerals might be a red flag for malfeasance.
Please note: This item is from our archives and was published in 2018. It is provided for historical reference. The content may be out of date and links may no longer function.

Related
Lessons in internal control lapses from major fraud cases
Fraud and technology: How to handle the double-edged sword
Writing an effective AI prompt for an audit
Three types of fraud schemes are of special interest to CPAs — financial statement fraud, occupational fraud, and bribery. Many, but not all, of these types of fraud schemes require the fraudster to invent a series of fraudulent numbers in the execution of the scheme. CPAs who know how to spot the fingerprints of these fabricated numbers will have an edge in the fight against fraud.
This article looks at a fingerprint of fraudulent numbers that might seem obvious but is often overlooked: Fraudulent numbers are frequently round numbers.
An appreciation of the overuse of round numbers by fraudsters may benefit internal auditors and forensic accountants who are proactively looking for fraud and bribery schemes as a part of a continuous monitoring program. External auditors could run round number audit data analytics tests in the planning phase of an audit that are designed, in part, to assess the risk of material misstatements. These round number tests could also be run in the audit’s testing phase as a test of controls and in the completion phase as a final review to detect possible misstatements.
Rounding to the nearest thousand or million dollars in financial statements, or to the nearest penny in earnings-per-share calculations, is done to make it easier for investors and other interested parties to focus on the important parts of the numbers. In a fraud fingerprint context, we are generally interested in transaction amounts or ledger balances that are exact multiples of $1,000 or $1,000,000. In the external auditing realm, AU-C Section 240, Consideration of Fraud in a Financial Statement Audit, requires journal entries to be examined for evidence of material misstatements due to fraud. AU-C Section 240.A49 states that inappropriate journal entries and other adjustments have characteristics that include the use of round numbers.
The AICPA’s new general ledger and subledger audit data standards, with their common framework, will help auditors to develop, over time, a level of experience and expertise with audit data analytics. Round number tests run against the currency fields in the ledgers could include extracting and scanning these records, as well as a comparison of the proportion of round numbers in the current period to that of prior periods. The prior periods, as is commonly done, could be used as the expectation formation for the round number testing, but it should be understood that any of the fraud types could be carried out with just a handful of round number transactions.
An analysis of round number transactions or balances is complicated by the fact that the round number universe includes legitimate and authentic transactions and balances. Experience has shown that round numbers are often linked to the purchase of goods or services with individual and unique features; used property, plant, and equipment purchases; and charitable or political campaign contributions. Precise numbers (such as $1,201.85) are often linked to the purchase of mass-produced items and amounts that are a result of a calculation (such as a property or income tax refund that includes interest). General ledgers and subledgers inevitably include legitimate entries that are round amounts. The challenge is to identify the fraudulent amounts that are the proverbial needles in a haystack, except that the fraud needles look similar to the hay. The next section of this article presents examples of round numbers used in fraud schemes and round numbers used in authentic data. This is followed by some tactical notes on running the analytics.
USES OF ROUND NUMBERS IN FRAUD SCHEMES
Financial statement fraud
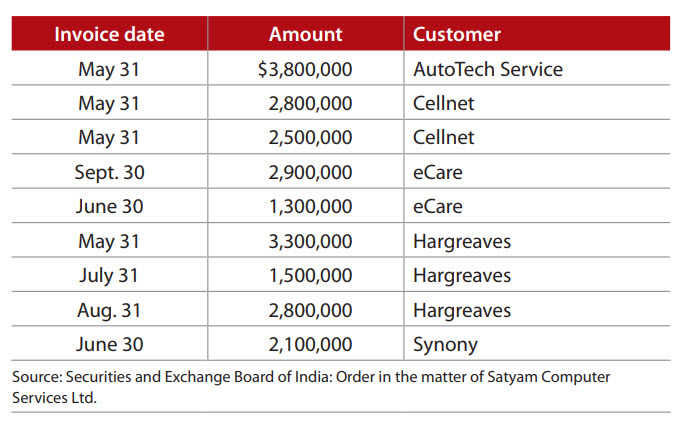
A classic case of round numbers being used to manipulate corporate earnings occurred at the India-based company Satyam Computer Services. In the Satyam fraud, which came to light in 2009, senior officers overstated earnings by booking fictitious revenues under fake company names. Sales invoices for nonexistent sales were reported as revenue and as accounts receivable in financial statements. The invoices were entered into the system by people who had a “superuser” status that allowed them to override system controls. These superusers recorded the sales in such a way that the invoices were not visible to the managers of the business units, who would have questioned the validity of the customers and the services provided.
Over the five-year life of the fraud (2003—2008) about 100 fictitious sales invoices were created each month. In 2006, a set of 27 false invoices was created by managers who were not superusers. The invented amounts were all multiples of $5,000 with nine invoices that were multiples of $100,000 (see the chart, “Round Numbers in Satyam Computer Services Fraud”). These round amounts would have been included in a listing of 2006 sales invoices and in the accounts receivable balances for 2006—2008. Auditors, internal and external, should look for round numbers and other red flags in systems with users who can override system controls.
Round numbers in Satyam Computer Services fraud
Ledger items with fictitious company names and amounts created by Satyam as part of a fraud scheme:
Occupational fraud
Harriette Walters, a tax office manager for the District of Columbia, embezzled more than $48 million in a scheme that ended only when a conscientious bank manager started asking questions. Over an 18-year period, Walters processed 239 fraudulent property tax refunds that ranged from $2,297.87 to $543,423.50 and used the proceeds to pay for a lavish lifestyle. These refunds were processed as if the property owner had won a dispute over the assessed value of his or her building. The refunded amount was based on the court-ordered reduction in the properties’ assessed value, a tax rate of 1.85%, and an interest rate of 6% for the period overpaid. Round number refunds should have been a rare event, but of the 163 fraudulent refunds processed by the district’s new, highly automated general ledger system, 15% were for multiples of $1,000. There also were three large refunds for $250,000, $250,000, and $350,000. (For more, see the sidebar “A MOD Way to Unearth Round Numbers in Excel.” The row 142 referenced there is the second time Walters used $250,000.)
Walters bypassed the new automated system by manually processing her fraudulent transactions. The oddly high percentage of round number entries was a red flag that could have been spotted much earlier if overseers had known what to look for and where.
A MOD way to unearth round numbers in Excel
The following is a look at how to find round numbers using Excel’s MOD function:
Label column E as Round. The formula in cell E142 is =IF(MOD(D142,1000)=0,1,0), as shown in the screenshot below.
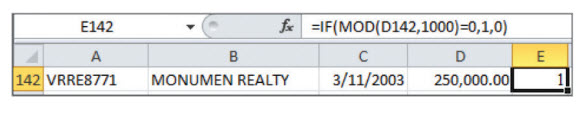
The column E formula returns 1 if the number is divisible by 1,000 and 0 otherwise.
To view only the round dollar amounts, the table could be sorted so that the 1’s in column E (the round numbers) are at the top of the sheet, or it could be filtered using a Number Filter to show only the rows where column E equals 1 (i.e., the round number records).
If a software package is used that does not have a MOD function, then the following formula in the fifth field could be used: =D142/1000.
A sixth field will then hold the round number indicator, and the formula there would be =If(E142-INT(E142)=0,1,0), where INT is the Integer function.
Bribery and corruption
The failure to detect bribes has implications related to contingent liabilities. In USA v. Rolls-Royce (2016), the company was found to have paid out $35 million in bribes to officials in several countries from 1989 to 2013. The court documents related to the bribes refer to round amounts such as $10,000, $100,000, $250,000, $500,000, $1,000,000, $2,000,000, and $3,000,000. However, any large multinational company would have thousands of transactions that are round dollar amounts. Some of the bribes were a round number percentage of the selling price. A bribe that is a round number in one currency will become a precise number if it is paid from a bank account in a different currency. The fines imposed due to the bribes wiped out some 13% of total stockholders’ equity.
ROUND NUMBERS IN AUTHENTIC DATA
Round numbers are also used in authentic transactions. An analysis of purchase-order data for Rochdale Borough in the U.K. examined a data set that had the details of 2,729 purchase orders with a maximum amount of £2.4 million ($3.24 million). The most frequently used amounts were all multiples of £1,000. Also, an analysis of city of Chicago purchase order data (available at data.cityofchicago.org showed that the most frequently used amounts were all multiples of $5,000 and $10,000. In contrast, purchase order data for the state of Virginia (available at data.virginia.gov) showed that only 7.3% of the amounts that were $1,000 and higher were multiples of $1,000. Purchase orders therefore use round numbers excessively but to varying degrees.
Bankruptcy filings include details of the gifts and charitable contributions made by a company prior to bankruptcy. Lehman Brothers data (available at dm.epiq11.com show that the company’s gifts and contributions schedule listed 3,127 gift amounts that ranged from $16 to $664,914. The most frequent amounts gifted were $100, $50, $2,000, $500, and $250, respectively. The number duplications show that the 15 most frequently used amounts were all multiples of either $25, $50, $100, $500, or $1,000. As you can see, round numbers are normal for this type of data.
HOW TO SPOT FRAUD WITH ROUND NUMBERS
The starting point of a proactive fraud detection exercise is for the CPA to have a test objective related to the data that will be analyzed. The CPA should then request and obtain a data file (see the AICPA’s Audit Data Standards at aicpa.org. The data file could include general ledger, accounts payable, or purchasing card transaction data for the period. The file should contain transaction amounts and other details such as debit/credit, date(s), source currency, payee (if applicable), ledger account class, ledger accounts debited or credited, business segment, and a description or memo field.
Data sets with up to 1,048,576 records could be analyzed in Excel while larger data sets would need alternatives such as CaseWare IDEA or Microsoft Access. The CPA should verify that the data file is complete, perhaps by reconciling the transaction totals to a credible independent source. General-ledger (journal-entry) data could be reconciled to the trial balance, and purchasing card data could be reconciled to the total amount paid to the card-issuing bank.
The CPA would then extract the round number transactions or balances that are, say, multiples of $1,000 or $1 million using the MOD function in Excel (see the sidebar “A MOD Way to Unearth Round Numbers in Excel”). The usual result is a sample that is too large to audit in its entirety. A recent analysis of the 3 million journal entries of a public company showed that 7,000 entries were multiples of $1,000. The ledger account balances of another public company with 55,000 ledger accounts showed that 500 of the balances were multiples of $1,000. The 100,000 accounts payable invoices of still another company included 2,000 invoice amounts that were multiples of $1,000. One option to keep the sample of notable items to a workable size is to focus the in-depth substantive tests to the amounts that are both large (the materiality consideration) and round (see the sidebar “How to Properly Log Large Round Numbers”).
How to properly log large round numbers
The following definition could be used to identify large round numbers:
Identify the maximum value in a data set, x, and calculate the log of x. If the maximum value was $875,592,640, then the log would be 8.9423. Let m be equal to the integer value of the log (8 is the integer value of 8.9423). Large round numbers would be numbers that are divisible by either 10m-1 or ½×10m-1. Here large round numbers would be numbers that were divisible by 107 and ½×107 ($10,000,000 and $5,000,000).
Auditors could use judgment here by, perhaps, excluding entries related to acquisitions and mergers, and closing entries when calculating the maximum value in a data file of journal entries.
Another option is to form groups of items with similar attributes and to focus on the high-risk groups. Transactions that are intra-company cost allocations might be low-risk, while journal entries processed soon after a quarter-end date could be high-risk. For example, in the ledger balances of the public company mentioned in the previous paragraph, there were 80 round number balances in the “prepaid expenses other, trade payables uninvoiced receipts” and “accrual other miscellaneous” accounts. The trade payables account was for accruing an expense that had not yet been invoiced by the supplier, and the accrual account was for “miscellaneous accrued liabilities awaiting final decision.” These accounts should rarely have been used and were known to be used by divisional controllers who were trying to be “creative.”
The smaller round dollar amounts should not be ignored. AU-C Section 240.A59 states that smaller misstatements, even with a cumulative effect that is not material, may indicate a risk of material misstatement due to fraud. Auditors need to consider whether the sum of the smaller amounts add up to a material amount, and auditors also need to pay attention to qualitative considerations in their evaluation of the materiality of uncorrected misstatements.
AU-C Section 240.13 states that the auditor may accept records and supporting documents as being genuine. This statement is not entirely applicable when CPAs are trying to detect occupational fraud or bribes. An internet search for “buy fake receipts” or “fake receipts” will show many websites that offer printing services that might assist fraudsters.
It is difficult to sketch an audit plan that would cover all the variations on the types of “billing schemes.” When identifying false claims for payment, forensic accountants can look for other analytics-related red flags:
- Vendors associated with false claims will not have a very low invoice count (people are greedy) or a very high invoice count (which increases the risk of detection). There would not be any credits against or adjustments to the invoiced amounts (because the transactions are fictitious).
- The total annual amount would not be too small (not worth the risk) or too big (and risk attracting attention). The upper end would be determined by the size of the victim company.
- Vendors associated with the false claims might have (almost) consecutively numbered invoices and an annual total that shows abnormal growth (people get greedier).
When vouching the paper invoices, CPAs should have a heightened skepticism for invoices related to services, paper invoices that are very basic (perhaps prepared in Microsoft Word) compared to what one would expect from a real company, invoices that appear sloppy and perhaps omit a physical address or other important details, and invoices with a vague description of the services provided.
CONCLUSION
Round number testing is relevant to AU-C Section 240; AU-C Section 315, Understanding the Entity and Its Environment and Assessing the Risks of Material Misstatement; and AU-C Section 520, Analytical Procedures. For journal-entry testing, firms could include round number testing in their audit program or audit manuals. The analysis could be included as a required step, an optional step, or something that is done on a rotation. The audit team could be allowed to exercise some judgment based on the size of the client and the auditor’s own risk appetite. As a substantive test or an analytical procedure, a round number analysis might even be applied to parts of the audit (one or more of the audit cycles). Here again, judgment could be used in making these determinations guided by the size of the client, the risk profile of the client, and the risk appetite of the auditor.
With respect to detailed substantive testing, a round number analysis could be run against the financial statement line items that use significant accounting estimates (allowances, accruals, sales returns, and so on). The test could be applied to selected ledger accounts. A relevant application could be to identify round numbers in selected ledger accounts, such as sales returns, accrual reversals, and allowance reversals, in the weeks after the relevant quarter.
Note that misstated financials could be accomplished with just, perhaps, 10 intentionally erroneous round number journal entries out of, perhaps, a universe of 2,000 valid round number journal entries. With many false positives, the auditor would need to use his or her understanding of the client and its business and apply strategic grouping and filtering to find the problematic entries. Firms need their own policies on whether to make these tests optional, required, or on rotation. Judgment would be needed based on the same factors and the size of the various accounting estimates.
Audit firms should provide focused and effective staff training that shows where and how round numbers have been used in frauds. This training could include discussing fraud and bribery case studies based on public records and possibly client data, and performing hands-on work using audit analytics tools to find the suspicious round dollar transactions.
About the author
Mark J. Nigrini (mark_nigrini@msn.com) is an assistant professor at West Virginia University in Morgantown, W.Va. His article “Lessons From an $8 Million Fraud,” co-written with Nathan J. Mueller, won the Lawler Award for best JofA article of 2014.
To comment on this article or to suggest an idea for another article, contact Jeff Drew, a JofA senior editor, at Jeff.Drew@aicpa-cima.com or 919-402-4056.
AICPA resources
Articles
- “What to Consider When Auditing Revenue Recognition Implementation,” JofA, Oct. 6, 2017
- “Lessons From an $8 Million Fraud,” JofA, Aug. 2014
Publications
- Codification of Statements on Auditing Standards (#ACODSAS17P, paperback; #ACODSAS17E, ebook)
- Guide to Audit Data Analytics (#ADATA17P, paperback; #ADATA17E, ebook; #ADATAO, online subscription)
- The Guide to Investigating Business Fraud (#056558, paperback only)
CPE self-study
- Fraud and Cash Receipts: Common Frauds and Internal Controls (#753347, text; #164791, online access; #GT-CL4RCR, group pricing)
Conferences
- Practitioners Symposium and Tech+ Conference at AICPA Engage, June 11—14, Las Vegas
- AICPA Forensic & Valuation Services Conference, Nov. 5—7, Atlanta
Webcast
- Excel for Accounting Professionals Webcast Series, May 7, 2018 (#VCL2EXAP1803)
For more information or to make a purchase or register, go to aicpastore.com or call the Institute at 888-777-7077.
Webpage
- Audit Data Standards Library, aicpa.org
FVS Section and CFF credential
Membership in the Forensic and Valuation Services (FVS) Section provides access to numerous specialized resources in the forensic and valuation services discipline areas, including practice guides, and exclusive member discounts for products and events. Visit the FVS Center at aicpa.org/FVS. Members with a specialization in forensic accounting may be interested in applying for the Certified in Financial Forensics (CFF) credential. Information about the CFF credential program is available at aicpa.org/CFF.
OTHER RESOURCES
Articles
- “The Implications of the Similarity Between Fraud Numbers and the Numbers in Financial Accounting Textbooks and Test Banks,” by Mark Nigrini, Journal of Forensic Accounting Research, Vol. 1, Issue 1 (December 2016).
- “Satyam Fraud: A Case Study of India’s Enron,” by Veena Brown, Brian Daugherty, and Julie Persellin, Issues in Accounting Education, Vol. 29, Issue 3 (August 2014).
Publications
- Forensic Analytics: Methods and Techniques for Forensic Accounting Investigations, by Mark Nigrini (John Wiley & Sons 2011)
- Order in the matter of Satyam Computer Services Ltd., The Securities and Exchange Board of India (2014)
Website
- Audit Data Analytics. Chartered Professional Accountants of Canada (CPA Canada), cpacanada.ca
- Public Access to Court Electronic Records, pacer.gov
- U.K. Serious Fraud Office, case documents related to the Rolls-Royce investigation, sfo.gov.uk/cases/rolls-royce-plc


















